While your Sophos Firewall is a security product, it also needs to be secured. Follow these best practices to optimize the security of your network.
Your Firewall is the heart of your network helping secure it from risks and threats. And while it’s a security product, and a critically important one, it also needs to be secured. This article outlines some of the best practices for hardening your Sophos Firewall.
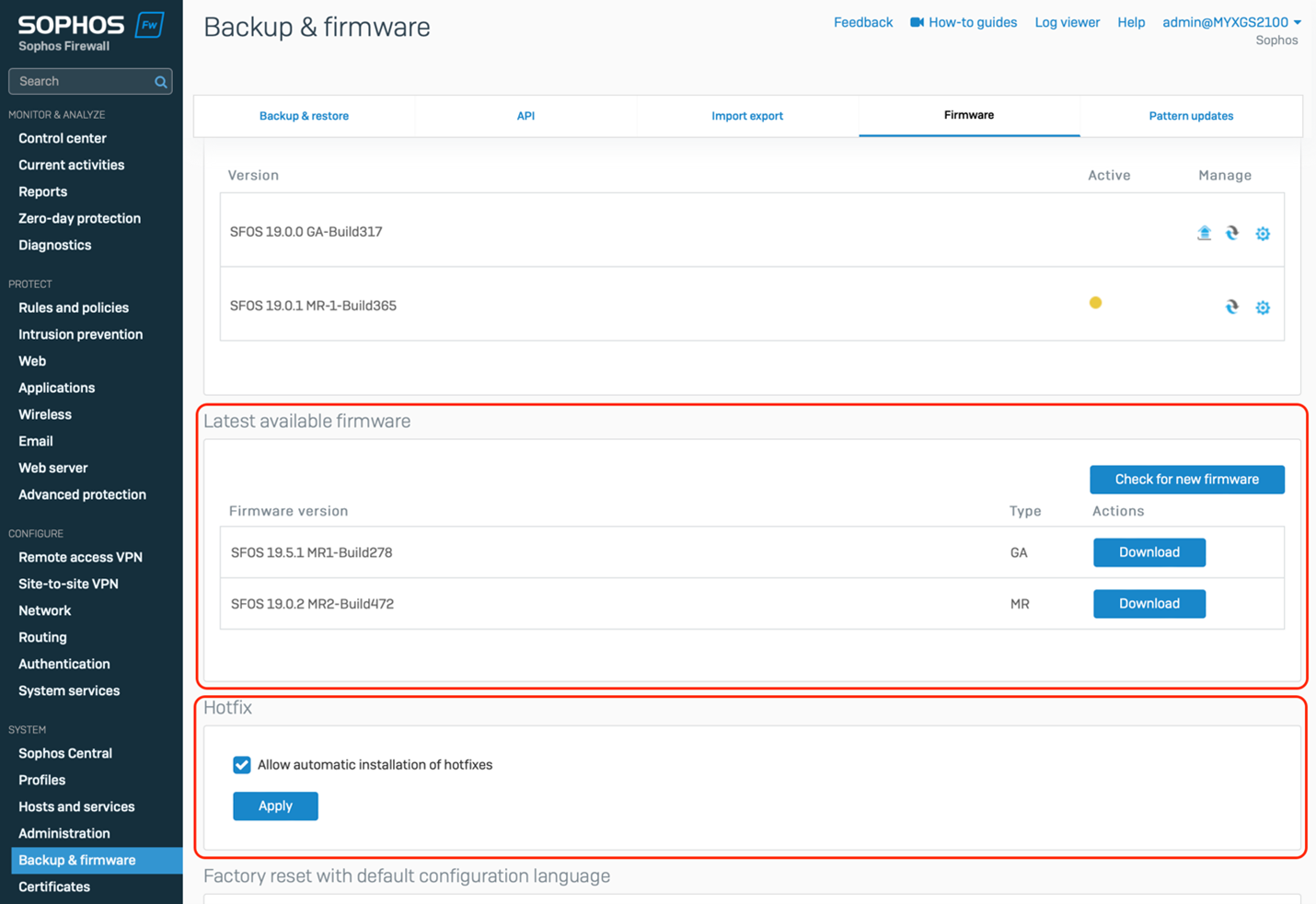
1. Update The Firmware with Every Release
If you only take away one thing from this article, it’s this. And this recommendation doesn’t just apply to your firewall, but all of your networking infrastructure. Most Sophos Firewall OS firmware updates include important security fixes. The best way to harden your firewall is to ensure it’s running the latest firmware. For Sophos Firewall, we just released v19.5 MR1 which includes a number of great new features, a significant performance boost, and several fixes. You can always find the latest firmware release for your firewall simply by navigating to Backup and Firmware > Firmware (as shown below).
2. Enable Hotfixes
Occasionally, patches for vulnerabilities and other security fixes are released between regular firmware updates. This is done by applying hotfixes to your firewall automatically so its vitally important that this feature be enabled on your firewall. While it’s enabled by default, some customers have disabled this. If you are one of those, it’s highly recommended you go back and turn this feature on. This feature is found by navigating toBackup and Firmware > Firmware – check that “ Allow automatic installation of hotfixes” is enabled (as highlighted at the bottom of the screen shot above).
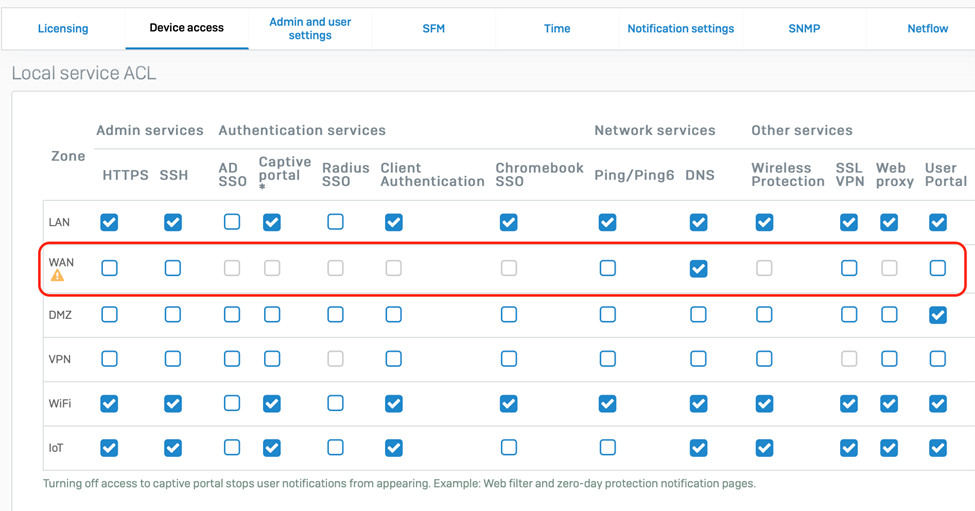
3. Limit Access to Firewall Services
Your Firewall offers a number of ways to limit access to services that are not required to reduce your exposure on the WAN. You should periodically check the device access settings and ensure that all unnecessary services are disabled (unchecked) on the WAN (see screen shot below). In particular, it’s strongly recommended that you disable remote admin via HTTPS and SSH, as well as the Captive Portal and User Portal on the WAN. Use Sophos Central, VPN or ZTNA to manage your firewall remotely. See the product documentation for instructions on how to manage device access.
4. Utilize Multi-Factor Authentication and Role-Based Administration
Enable multi-factor authentication (MFA) or one-time-passwords (OTP) and enforce strong passwords to protect your firewall from unauthorized access from stolen credentials or brute force hacking attempts. Sophos Firewall supports a rich set of MFA authentication options including new Azure AD single-sign-on authentication for webadmin access which can be super convenient ( video / documentation ).
You should also consider taking advantage of Sophos Firewall’s granular role-based administration profiles to limit access for administrators of the firewall. Provide read-only access to administrators that don’t absolutely need control over various firewall functions.
5. Additional Best Practices for Securing Your Network from Ransomware
While you’re looking at ways to better secure your network, I suggest you take a look at our recommended best-practices for securing your broader network from the latest ransomware and other advanced threats. If you’re a Sophos Firewall customer, you’re already well on your way to better protecting your network, but there may be other Sophos solutions you’re overlooking that can further help secure your organization.
Download the Guide to get the full set of best practices.